You and possibly a CS1321 classmate are to implement a doubly-linked list class using dynamic memory and links. Although similar to the dll doubly-linked list class presented in lecture, your class's implementation is to be linear and may not have a sentinel. This implementation is the one programmers usually use if they do not know about the circular implementation with a sentinel.
A doubly-linked list is a data structure with objects arranged in linear order and permitting easy access to both previous and next items. For example, the STL list class implements a doubly-linked list. (Interestingly, STL creator Alex Stepanov apparently also decided to use a circular implementation with a sentinel.)
Your implementation should support the same operations as the dll doubly-linked list class presented in lecture plus a few more. That is, it should support all the operations listed in Table 1. When inserting an item into a list, the item's new link should be to the left of the user-specified position. If this position is a ground (null) pointer, one should insert at the list's right end. To insert at the left end, the user should specify the leftmost link. To erase a link, the user need only specify the link to erase. Unlike the implementation presented in class, insert should return a pointer to the inserted link. The erase() function returns the link to the right of the erased link or a ground if the rightmost link was removed. Both functions may assume that their parameter values are valid.
The last four operations permit the user to ``move'' through the items in the list. begin and end return pointers to a list's first link and one past its last link, respectively. Given a pointer into the list, pred and succ return pointers to the preceding link (link to the left), and subsequent link (link to the right), respectively. The predecessor of the leftmost link is a ground pointer as is the successor of the rightmost link. When given a ground pointer, pred assumes the ground is the right end of the list. When given a ground pointer, succ assumes the ground is the beginning of the list.
Please ensure that, if a list is copied, changing the original list's contents does not change the copy and vice versa. (Hint: Write an assignment operator and a copy constructor if necessary.) Be sure not to leak dynamic memory. (Hint: Write a destructor function if necessary.)
For now, assume the list contains chars, but, anticipating future modification to hold any particular type, we require using item_type.
In class, we presented algorithms and code ( dll.h) for a circular implementation with a sentinel link. In this assignment, we will use a linear implementation with no sentinel. For example, here are
(Note: I prefer to reference null pointers using the macro NULL, which can be found in library include file cstddef. To do this, include the line
#include <cstddef>
You can then write code such as the following
int * p;
p = NULL;
if (p == NULL) cout << "p null\n";
Or you can omit the #include and replace NULL
with 0.)
The linear implementation will be very similar to the circular, sentinel implementation except that the routines cannot always assume that there is a link to the left and right when inserting and erasing. For example, consider inserting a link at the right end of a list with one link. We are given a ground pointer. Assume we have already created a link named n to hold the new item.
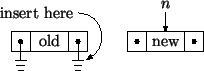
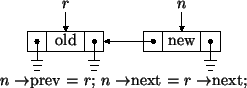
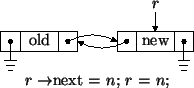
Your implementation should support insertion and erasure anywhere in a list, e.g., at the beginning, middle, or end, for a list of any length, e.g., empty, one link, or multiple links. Before writing code, we strongly recommend that you draw pictures of all possible cases and annotate with the associated code. Otherwise, the probability of obtaining a correct implementation is minimal.
Our recommended strategy for implementing and testing your code is to interleave writing member functions, compiling, and testing. That is, choose an order for implementing member functions that minimizes the amount of code written between compilations and testing.
After you have finished the implementation, try using the buffer code. It uses a dll class but assumes that member functions link * begin(void) const and link * end(void) const are also * defined (which they will be in your revised class). editor.cc uses the buffer class to implement the brain-dead string editor presented in lecture.
Your implementation should correctly use dynamic memory. For example, dynamic memory should be deleted when no longer used, and deleted memory should not be used. If you wish to use the mtrace command to help find memory-use errors, here are the instructions for doing so:
#include <mcheck.h>
and, at the beginning of main(), add
mtrace();
Let's assume the executable is named a.out.
declare -x MALLOC_TRACE=foo.txt
in a shell. (You can replace foo.txt with any desired
file name.)
mtrace a.out $MALLOC_TRACE
in the same shell.
Caveats:
We suggest starting with the circular, sentinel implementation dll.h and converting it to a linear implementation.
The lecture version of the buffer code has been modified to use begin, end, pred, and succ. Revised code can be found in this link to buffer.h.
As for previous homeworks, working with other people during your planning phase is encouraged. For this homework, you are permitted to write the code, i.e., program, with one other person in CS1321. To learn the material, both of you should be actively involved in the programming. Failure to do so will almost certainly hurt your comprehension of the material in the rest of the course.
Each one- or two-person team of programmers should submit only its completed implementation in a file named dll.h. You need not send any other files. Please send only text documents, do not send Microsoft Word documents, PDF documents, HTML documents, etc. Please include both your names and email addresses at the top of your program.
We will test your code using our own main() function. Please be sure it compiles without warning when using g++ -Wall -pedantic.
See the guidelines for programming assignments for instructions on how to e-mail the programs. For this assignment use a subject line of ``cs1321 homework 6''.
If a team of two are in different sections, submit exactly once to one of the two permissible email addresses.